In today’s rapidly evolving digital landscape, where unprecedented amounts of data traverse through complex networks, ensuring robust cybersecurity has become more crucial than ever. With cyber threats growing in sophistication and frequency, businesses are increasingly turning towards innovative solutions to safeguard their assets. Enter the world of cloud-based threat monitoring solutions—a groundbreaking approach that provides real-time surveillance and protection against cyber threats from anywhere, at any time. By leveraging the power and scalability of cloud technologies, organizations can not only enhance their security posture but also achieve cost-effective monitoring with minimal on-premise infrastructure.
Moreover, businesses are no longer constrained by geographical boundaries when it comes to deploying effective threat monitoring solutions. The cloud-based approach provides an unparalleled level of agility, allowing teams to quickly adapt and respond to threats, irrespective of their physical location. Whether it’s a small startup or a large multinational corporation, these solutions offer a customizable and scalable security framework tailored to the unique needs and risks faced by each organization. As the cyber threat landscape continues to expand, the adoption of cloud-based threat monitoring solutions is not just a choice but a necessity for businesses aiming to protect their valuable data and ensure uninterrupted operations.
Why Cloud-Based Threat Monitoring Solutions are Essential
In an era where data breaches can have catastrophic consequences, cloud-based threat monitoring solutions have emerged as an indispensable ally in the fight against cybercrime. These solutions offer not only real-time threat detection and alerting but also foster a proactive security culture by enabling continuous monitoring and rapid incident response. More so, the integration of artificial intelligence and machine learning enhances the capability of these solutions, providing predictive analysis that helps identify potential threats even before they materialize. Such intelligent systems can adapt to the dynamic threat environment, learning from past incidents to enhance future threat detection and mitigation efforts.
As cybersecurity continues to dominate headlines, the demand for efficient and reliable security measures is on the rise. Cloud-based threat monitoring solutions present organizations with the opportunity to stay one step ahead of cybercriminals. With their flexibility, scalability, and cutting-edge technology, these solutions empower businesses to protect their network edges and ensure compliance with regulatory requirements, ultimately maintaining trust and confidence amongst their clientele.
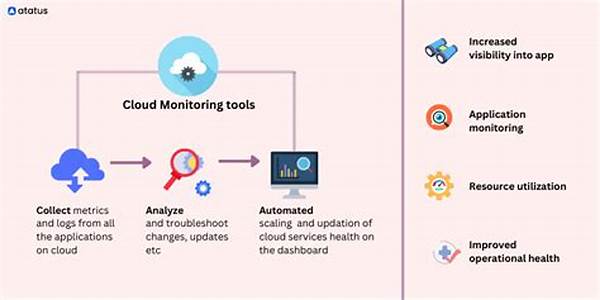
Exploring the Benefits of Cloud-Based Threat Monitoring
The pursuit of robust cybersecurity strategies has driven firms to explore innovative technological solutions. Among these, cloud-based threat monitoring solutions have proven to be effective defenses against the myriad of cyber threats faced by today’s digital businesses. Firstly, these solutions provide real-time visibility into network traffic, allowing organizations to detect and respond to threats promptly. This immediate insight is invaluable, especially for businesses with complex network architectures, enabling remedial actions before security breaches can escalate.
Furthermore, cost efficiency is a significant advantage. By utilizing cloud infrastructure, businesses can avoid the substantial capital expenditures associated with maintaining physical security infrastructure on-premises. Instead, they pay for the service on a subscription basis, making it more manageable and predictable. The scalability of cloud-based threat monitoring solutions ensures that businesses can easily expand their coverage as they grow, without facing the limitations or costs of physical infrastructure expansion.
Additionally, the ease of use and deployment cannot be overstated. With cloud-based solutions, companies can bypass the cumbersome installation processes traditionally associated with cybersecurity tools. Deployment is quick, often with minimal downtime, and updates are managed automatically, ensuring systems are always up-to-date with the latest threat intelligence. This convenience allows IT teams to focus on strategic initiatives rather than routine maintenance tasks, maximizing their productivity.
In consideration of all these benefits, there is a compelling case for businesses to transition to cloud-based threat monitoring solutions. Not only do they offer protection and peace of mind, but they also provide a competitive edge in today’s digital-first business environment, where cybersecurity is paramount to organizational success.
The Versatility of Cloud-Based Threat Monitoring Solutions
Skills Required for Navigating Cloud-Based Threat Monitoring
Navigating the world of cloud-based threat monitoring solutions requires a range of skills. Fundamentally, cybersecurity expertise is crucial. Individuals must have a strong understanding of cyber threats, vulnerabilities, and protective measures to effectively leverage these solutions. Knowledge of network architecture and data protection mechanisms is also essential, enabling professionals to configure and optimize security settings in line with organizational requirements.
Furthermore, analytical skills play a vital role. Security professionals must be able to interpret complex data and identify patterns indicative of potential threats. This ability is further enhanced by familiarity with AI and machine learning technologies, which are increasingly integrated into cloud-based threat monitoring systems. Being able to understand and utilize these technologies can significantly enhance the effectiveness of threat detection and prevention measures.
Moreover, practical problem-solving skills are of the essence. The rapid nature of cyber incidents requires quick thinking and decision-making. IT teams must be adept at troubleshooting, able to swiftly devise solutions when unexpected issues arise. They must also maintain a keen awareness of emerging trends in the cybersecurity domain, ensuring their strategies align with current and future threats.
Continuing education and training are vital for professionals working with cloud-based threat monitoring solutions. The cybersecurity landscape is ever-changing, necessitating ongoing learning and adaptation. By enhancing their skills and keeping up-to-date with industry developments, individuals can maximize the effectiveness of these powerful security tools, ultimately safeguarding their organizations from pressing cyber threats.