Hey there, tech enthusiasts and digital custodians! Ever heard the saying, “Don’t put all your eggs in one basket”? Well, the same logic applies when it comes to securing your digital assets. Diving into the implementation of layered security strategies is like giving your data a snug, multi-layered blanket of security. It’s not about just one fix; it’s about having a backup to your backup’s backup. Let’s unravel the beauty behind these multiple layers and how they safeguard against the most mischievous cyber threats.
Understanding Layered Security
To truly appreciate the implementation of layered security strategies, think of it like building a fort for your childhood secrets. Each layer of security is designed to protect against different types of intrusions, ensuring that if one barrier fails, others remain intact. By employing multiple layers, any single vulnerability is less likely to jeopardize the overall security. This strategy is akin to setting up traps for uninvited guests—different types of traps for different types of intruders. From firewalls to antivirus software and encryption protocols, every measure works in harmony to shield valuable data, offering peace of mind in an ever-connected world.
In essence, implementing layered security strategies means not leaving your digital door wide open. You wouldn’t rely on a single key to keep out burglars, and the same goes for cyber threats. A layered approach puts multiple safety nets in place. When one net isn’t quite strong enough, others are ready to catch the slack. It’s this intricate choreography of security layers that ensures robust defense, keeping you a step ahead of would-be attackers.
Key Components in Layered Security Strategies
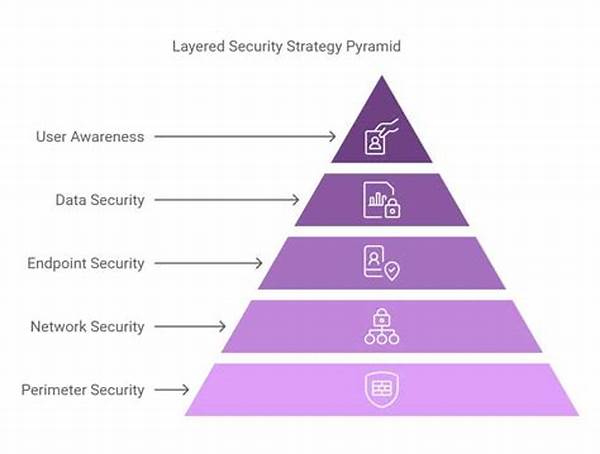
1. Firewalls Galore: The implementation of layered security strategies starts with firewalls. Picture them as the doormen to your digital fortress, deciding who gets to come in and who stays out.
2. Antivirus Armor: A good antivirus program is like having a knight in shining armor that fights off nasty viruses, part of that robust implementation of layered security strategies.
3. Encryption Protocols: Imagine your data is a secret recipe. Encryption transforms it into an indecipherable code, safeguarding your treasures as an essential element of the implementation of layered security strategies.
4. Two-Factor Authentication: Because one password isn’t enough, enter the superheroes of security requiring two forms of identity to grant access—making them a critical part of the implementation of layered security strategies.
5. Regular Updates: This aspect of the implementation of layered security strategies might be the least glamorous but is just as essential. Keeping systems updated guards against newly emerging threats.
The Benefits of Implementing Layered Security
Now, let’s chat about why the implementation of layered security strategies is a game-changer. Firstly, it acts as a bouncer for your networks, diligently working to filter out unwanted visitors and signals. Think of it as having a secret service for your data. By overlapping layers of security, gaps are significantly reduced. This means that even if a cybercriminal manages to navigate through one layer, they’re stumped by another.
Moreover, implementing layered security strategies ensures redundancy. If one security measure goes down, others are instantly in place to take over. It’s about more than just creating a maze for hackers; it’s about weaving a web where every strand contributes to your data’s overall protection. It’s a proactive stance rather than a reactive one, constantly adapting to new threats.
Challenges in Implementing Layered Security
Venturing into the implementation of layered security strategies isn’t all smooth sailing—it has its hurdles. The integration of multiple security layers can sometimes lead to complexity that bogs down systems or confuses users. Balancing the intricacies of different security measures while maintaining ease of use is no small feat. However, simplifying user experience without compromising on security remains paramount for success.
Another challenge is ensuring compatibility between different security solutions. Manufacturers often have unique systems that may not play nice with each other right out of the box. The challenge lies in finding compatible features that work in harmony, making the transition into layered security a seamless one. It’s crucial to stay informed and flexible to handle these challenges as they arise.
Real-World Applications of Layered Security
In the practical world, the implementation of layered security strategies is very much alive and kicking. Consider big-name corporations—they employ a myriad of protective measures to ensure their enormous databases remain untouched. By merging firewalls, encryption, biometric access, and more, they build impregnable walls around their cyber valuables. But it’s not just tech giants benefiting—individuals and small businesses, too, leverage these strategies for peace of mind.
Moreover, industries like finance and healthcare, where data sensitivity is paramount, rely heavily on layered security. In these sectors, even minor breaches could lead to catastrophic outcomes—making the implementation of layered security strategies an absolute must. It’s not just about prevention; it’s about maintaining operational integrity and trust.
Streamlining Your Own Layered Security
If you’re like me, and all this tech talk makes your eyes gloss over, worry not! Simplifying the implementation of layered security strategies can be approachable. Start with practical steps: enable firewalls on all devices, regularly update software, and embrace two-factor authentication wherever possible. By adopting these basic layers, you’re already making significant strides.
Consistency is key in maintaining a strong defense. Encourage regular security sweeps and keep your team informed of the latest threat landscapes. Remember, whether big or small, no organization is immune to threats. But with the right layering, you can stand tall in the face of challenges, armed with a formidable digital shield.
Conclusion of Layered Security Implementation
In summary, the implementation of layered security strategies is akin to constructing a fortress around your data. It’s about more than just stacking defenses; it’s about ensuring that each layer complements one another, creating a cohesive and thorough protective tapestry. Each layer plays its part, contributing to an overall robust defense system.
Ultimately, a layered security approach is about staying a step ahead of potential threats. Technology and cyber threats will continue to evolve, but with a solid, adaptable defense in place, you can meet new challenges head-on. It’s about peace of mind, knowing your data is wrapped in multiple layers of security, ready to thwart any villain that comes its way.