- Threat Intelligence Tools and Solutions Overview
- In-Depth Analysis of Threat Intelligence Tools and Solutions
- Actionable Steps Derived From the Threat Intelligence Overview
- Expounding the Necessity of Threat Intelligence Solutions
Threat Intelligence Tools and Solutions Overview
In today’s rapidly evolving digital landscape, cybersecurity has risen to prominence, not as a mere protective measure but as a fundamental business requirement. Organizations, regardless of size or industry, face an ever-increasing array of cyber threats that can compromise sensitive data, disrupt operations, and damage reputations. In response, the demand for threat intelligence tools and solutions has skyrocketed. These tools provide organizations with critical insights into potential threats, helping them anticipate, prepare for, and effectively respond to cyber incidents. A comprehensive threat intelligence tools and solutions overview is thus essential for any entity seeking to safeguard its digital assets.
The essence of threat intelligence lies in its ability to convert raw data into usable information regarding potential threats. This conversion process involves collecting and analyzing data on a global scale—from dark web forums to sophisticated malware analysis. The result is actionable intelligence that informs decision-making processes and enhances an organization’s security posture. Through the use of state-of-the-art technologies, threat intelligence solutions offer insights into threat actors’ methodologies, so businesses can reinforce their defenses proactively.
Many organizations still underestimate the importance of threat intelligence solutions. However, those at the forefront of cybersecurity strategy often emphasize their significance as a cornerstone of security infrastructure. With cyber threats growing more advanced and prevalent by the day, relying on traditional defense mechanisms like firewalls and antivirus software is no longer sufficient. Effective threat intelligence tools empower you to take pre-emptive actions, mitigating risks before they materialize into costly breaches.
An effective marketing strategy for threat intelligence tools involves highlighting their unique benefits. Imagine a service that not only warns you about imminent dangers but also provides a detailed roadmap to avoid them—a dream come true for any enterprise weary of unpredictable cyber threats. By focusing on the gains in operational efficiency, risk reduction, and peace of mind, vendors can convince potential customers of the value of adopting these solutions.
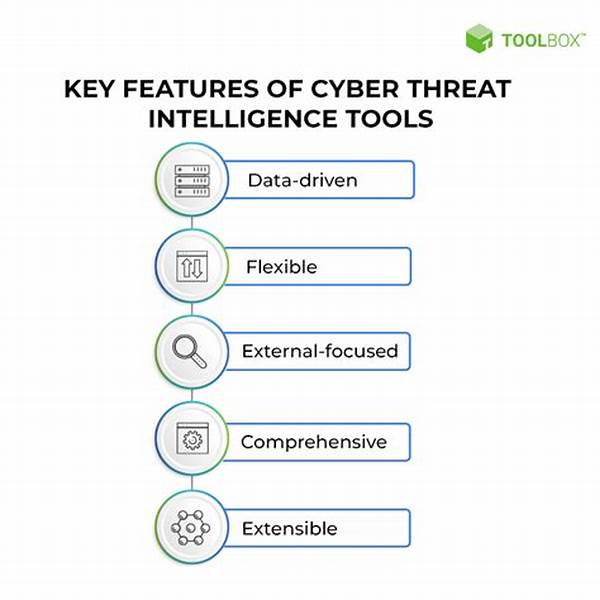
Key Features and Benefits of Threat Intelligence Tools
Understanding the impact and utility of threat intelligence tools requires exploring their features and benefits in detail. These tools are equipped with a variety of functionalities designed to enhance an organizations’ capability to safeguard its infrastructure.
In conclusion, this threat intelligence tools and solutions overview highlights the necessity for corporations to invest in robust cybersecurity measures. With the right tools, companies can transform their approach from a reactive stance to a predictive one, preparing for and mitigating threats well before they occur. Emphasizing both the analytical and anticipatory benefits of these solutions can capture the interest of executives and IT leaders alike, driving them to take action and secure their futures.
—
In-Depth Analysis of Threat Intelligence Tools and Solutions
Crafting a detailed threat intelligence tools and solutions overview involves dissecting the various types of tools available in the market and understanding their specific contributions to cybersecurity protocols. Organizations can choose from a range of tools, each varying in complexity and offering tailored to meet diverse security needs, from SMEs to global enterprises. This section will explore the top-tier tools and analyze their core competencies.
Different Types of Threat Intelligence Solutions
Threat intelligence solutions can be broadly categorized into three main types: strategic, tactical, and operational. Strategic threat intelligence provides a high-level analysis of risks that impact an organization’s business goals. In contrast, tactical threat intelligence focuses on examining threat actors’ methodologies and tactical details. Finally, operational intelligence deals with real-time monitoring and response to immediate threats.
The scope of these solutions manifests in comprehensive platforms that offer integration with existing security infrastructures, predictive analytics to anticipate future threats, and automated incident response capabilities. For instance, many solutions now feature AI-driven engines that can process vast datasets and identify patterns of malicious activity faster than any human could.
Selecting the Right Threat Intelligence Tool
Picking the right tool depends on the organization’s specific needs and current security architecture. While some might require a robust end-to-end platform, others might benefit from specialized tools designed for niche threats. This involves evaluating factors such as ease of integration, scalability, user-friendliness, and cost-effectiveness.
Organizations should also consider the vendor’s track record, industry reputation, and customer support services. In the era of cloud-based solutions, scalability and seamless updates are crucial—features that should be integral to any high-quality threat intelligence tool.
Overall, having a comprehensive threat intelligence tools and solutions overview can significantly enhance an organization’s proactive security measures, mitigating risks and protecting vital data from evolving cyber threats.
—
Actionable Steps Derived From the Threat Intelligence Overview
Here are six practical actions to consider when utilizing threat intelligence tools and solutions:
The Imperative of Understanding Threat Intelligence Tools
As the digital realm expands, so does the complexity of cyber threats. Organizations must recognize the essentiality of incorporating advanced threat intelligence solutions into their cybersecurity strategies. Such tools not only serve a defensive role but also a transformative one, enabling entities to shift towards a predictive, rather than reactive, stance in combating cybercrime. This evolution is all the more crucial for maintaining consumer trust, safeguarding reputation, and ensuring compliance with increasingly stringent data protection regulations.
In a landscape where a breach can be both financially and reputationally costly, taking proactive steps based on accurate threat intelligence is an investment in the organization’s longevity and security.
—
Expounding the Necessity of Threat Intelligence Solutions
While the words “threat intelligence tools and solutions overview” might initially conjure images of highly technical processes and jargon-heavy discourse, the reality is that these solutions are both accessible and essential for businesses across the spectrum. Investing in such tools is akin to purchasing an insurance policy not just for data protection, but also for sustaining trust, credibility, and a seamless customer experience.
Research and Real-World Applications
Research underscores the importance of integrating threat intelligence as part of an organization’s core strategy. Studies reveal that firms employing comprehensive threat intelligence platforms effectively reduce the average cost of a data breach by significant margins. Additionally, these companies exhibit quicker recovery times and minimize downtime post-incident.
The Role of Threat Intelligence in Modern Cybersecurity
To further elucidate, imagine a fictional company, TechSolutions Inc., which recently integrated a leading threat intelligence platform. In facing potential threats from ransomware to phishing efforts, their advanced system provided real-time alerts and insights, outfits the security team could act upon preemptively. These capabilities ensured that TechSolutions Inc. not only mitigated a crisis but also avoided potential revenue loss, showcasing the practical benefits of having a threat intelligence solution in place.
—
Here are six short explanations concerning threat intelligence tools and solutions overview:
Expanding the Benefits of Threat Intelligence Tools
The practical benefits of threat intelligence tools and solutions extend far beyond technical advantages. They also elevate decision-making at the executive level by providing strategic insights into emerging threats. This way, organizations can prioritize investments in line with the potential business impact of different cyber risks. Furthermore, by embedding intelligence insights into daily operations, businesses engage every department in the collective effort to enhance security—transforming a potential vulnerability into a strategic asset.
Investing in these tools is not simply a technical decision but a strategic imperative. As companies increasingly rely on digital infrastructures, the value of safeguarding these assets cannot be overstated. Making this investment today is a step towards a more secure, resilient future.
—
Exploring Threat Intelligence and Solutions for Organizations
An all-encompassing threat intelligence tools and solutions overview provides businesses with a strategic advantage in anticipating and thwarting cyber threats. With the cyber threat landscape becoming increasingly sophisticated, companies can no longer be complacent with basic measures. The anatomy of modern threat intelligence solutions reveals a blend of both technical prowess and strategic insights essential for countering today’s cyber adversities.
The Intersection of AI and Threat Intelligence
Artificial intelligence has redefined threat detection and response, automating complex data analyses that would overwhelm human capacities. Companies deploying AI-enhanced threat intelligence tools gain a strategic edge, enabling faster response times and more accurate threat assessments. Importantly, this integration not only improves immediate detection but also refines long-term cybersecurity strategies.
Steps to Implementing Threat Intelligence Solutions
For organizations yet to embark on this journey, the transition to incorporating threat intelligence needs strategic planning. Start by mapping existing vulnerabilities and aligning them with the functionalities offered by leading solutions. Engage stakeholders across departments to buy into the necessity of enhanced security measures and foster a collective effort towards implementation.
With comprehensive threat intelligence tools, companies can convert potential threats into actionable insights, bolstering their cyber defenses with holistic strategies. Embracing these solutions opens a new frontier in cybersecurity—a domain where proactive threat mitigation becomes the standard, paving the way for secure and resilient digital enterprises.