In the digital age we live in today, where cyber threats are more sophisticated and rampant than ever, continuous security monitoring frameworks are essential for businesses of all sizes. These frameworks offer a structured approach to safeguarding information assets, minimizing the risk of security breaches, and ensuring compliance with regulatory requirements. Understanding continuous security monitoring frameworks is not just a necessity but a strategic advantage in a world driven by data.
Continuous security monitoring frameworks are designed to provide real-time visibility into an organization’s IT infrastructure, allowing for the detection and mitigation of potential threats before they escalate. They operate on the principle that prevention is better than cure. Think about it as a continuous vigil, a virtual sentry that is always on the alert, always prepared. Unlike traditional security measures that often come into play post-incident, these frameworks focus on early detection and prevention, making them a game-changer in the realm of cybersecurity.
With the implementation of continuous security monitoring frameworks, businesses can proactively manage their security posture. This approach not only helps in identifying vulnerabilities but also aids in crafting strategies to address these weaknesses effectively. The real-time nature of these frameworks allows for the dynamic assessment of risks and provides actionable insights that are pivotal in decision-making processes. Imagine having an always-on detective working tirelessly to protect your digital assets. That’s the power of continuous security monitoring.
But how do we implement these frameworks effectively? It’s not just about installing the latest software or tools. It’s about creating a culture of security awareness, educating employees on best practices, and incorporating security considerations in every aspect of the business cycle. Continuous security monitoring frameworks should be tailored to fit the unique needs and structure of your organization. This is where the magic happens – when technological prowess meets strategic foresight.
Benefits of Continuous Security Monitoring Frameworks
The sheer pace at which technology evolves brings both incredible opportunities and unprecedented risks. Continuous security monitoring frameworks play a pivotal role in balancing this equation by offering a suite of benefits that extend beyond cybersecurity.
—
Goals of Continuous Security Monitoring Frameworks
In an increasingly interconnected world, the primary goal of continuous security monitoring frameworks is to safeguard organizational assets by providing round-the-clock surveillance of digital environments. By keeping an eagle eye on network activities and user behaviors, these frameworks serve as the frontline defense, ensuring that any suspicious activity is immediately flagged and addressed.
Continuous security monitoring frameworks aim to bolster the prevention and detection capabilities of an organization. They focus on early threat detection, crucial to minimizing the impact of security incidents. By keeping security professionals informed with timely updates and alerts, these frameworks empower organizations to react swiftly and efficiently, reducing downtime and potential damages.
Effective continuous security monitoring frameworks also strive to enhance compliance with regulatory standards. In today’s intricate web of data protection laws and industry mandates, staying compliant is non-negotiable. These frameworks help organizations effortlessly align with global and industry-specific regulations, avoiding hefty fines and preserving their reputation.
Moreover, continuous security monitoring frameworks aspire to foster a culture of proactive security awareness within organizations. By integrating security into the corporate DNA, they make security a shared responsibility, encouraging employees across all levels to be vigilant and responsible digital citizens.
Building Continuous Security Monitoring Frameworks
To achieve these goals, a tailored approach to building continuous security monitoring frameworks is essential. Simply put, your security strategy needs to be as unique as your business.
Empowering Through Continuous Monitoring
By empowering your team with cutting-edge tools and real-time insights, continuous security monitoring frameworks transform security from a daunting challenge into a manageable, dynamic component of your business.
—
1. Proactive Threat Identification
2. Real-Time Alerts and Notifications
3. Comprehensive Risk Assessment
4. Regulatory Compliance Management
5. Increased Efficiency and Cost-Effectiveness
6. User Behavior Analytics
7. Incident Response Optimization
The Architecture of Continuous Security Monitoring Frameworks
When we consider the structure of continuous security monitoring frameworks, it’s vital to understand that no single solution suits all. Some businesses require complex, multi-layered systems, while others thrive with more streamlined configurations.
Continuous security monitoring frameworks typically include a mix of specialized hardware, software, and human expertise. At the core, they leverage advanced analytics and artificial intelligence to identify anomalies and reveal security breaches at lightning speed. This blend of tools follows a layered security approach, addressing both external threats and internal vulnerabilities.
Streamlining the framework involves an initial assessment of the organization’s current security posture and identifying specific needs. From there, an iterative process of selecting and integrating technologies—such as intrusion detection systems, firewalls, and SIEM solutions—follows. The key to success in structuring effective frameworks lies in its adaptability, ensuring that as threats evolve, so does the framework.
—
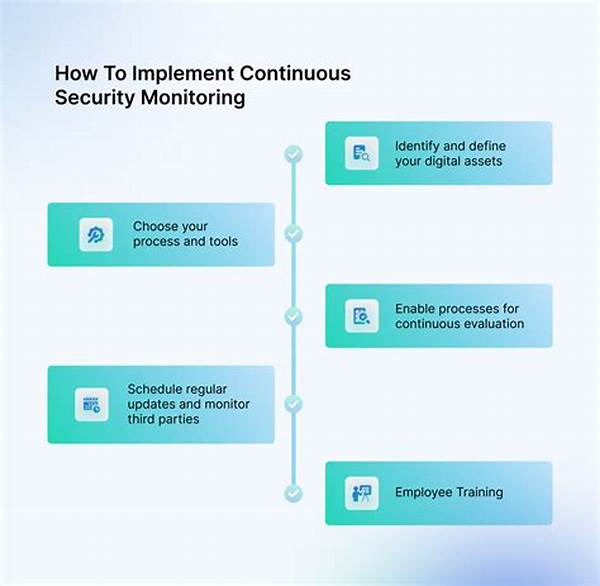
Implementing Effective Continuous Security Monitoring Frameworks
Implementing continuous security monitoring frameworks involves strategic planning and detailed knowledge of the business’s technology infrastructure. Whether a company is sprawling or a startup, the core principle remains the same: proactive prevention over reactive management.
Digital Sentinels on Duty
In today’s intricate digital landscape, continuous security monitoring frameworks act like digital sentinels, standing guard 24/7, vigilantly watching over your digital kingdom.
The Mantra of Proactive Security
The mantra driving these potent frameworks is simple yet powerful: act before a threat becomes an incident. They are the quiet heroes of the corporate world, unseen yet ever-critical, ensuring business continuity and integrity. With powerful continuous security monitoring frameworks, businesses don’t just guard against breaches—they build fortresses of trust.
Security is evolving, and how we implement continuous security monitoring frameworks today will dictate how well-prepared we are for the threats of tomorrow. It’s an exciting time, a time for businesses to take control of their digital destinies.
Key Features of Continuous Security Monitoring Frameworks
Continuous security monitoring frameworks are not just tools; they are vital components of modern business strategy. As the digital frontier continues to expand, these frameworks empower organizations to stand robust and ready, ensuring a future where technology is both a tool and an ally.