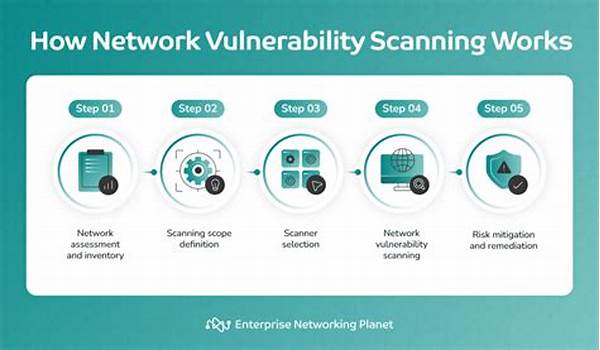
In today’s fast-paced digital landscape, safeguarding your network is of paramount importance. The network vulnerability scanning processes are pivotal in identifying and mitigating any potential weaknesses before cybercriminals exploit them. This article delves into the effective methodologies that enterprises use to ensure their networks remain secure, efficient, and trustworthy. But why should you care? Picture your business as a grand castle. Without a sturdy wall (read: a secure network), intruders can easily walk in and plunder at will. Our network vulnerability scanning processes act as knights watching diligently from the high towers of your digital fortress, vigilantly ready to deter any threats.
Businesses today cannot afford to overlook network security. Cyber threats lurk around every corner, from small startups to major corporations. Implementing robust network vulnerability scanning processes is essential to staying ahead of adversaries. These processes involve routinely checking for security gaps, ensuring compliance with regulations, and enhancing overall security postures. They empower businesses to avoid costly breaches and maintain client trust.
The implementation of network vulnerability scanning processes doesn’t have to be daunting. With advancements in scanning technologies, these processes have become more accessible and efficient. Organizations no longer need to dedicate vast resources or hire an army of IT experts to safeguard their networks. With automated solutions, businesses can deploy regular scans that alert them to vulnerabilities before they become a problem. The peace of mind this brings is invaluable, allowing companies to focus on growth without the constant fear of cyber threats.
The Importance of Regular Scans
Network vulnerability scanning processes should be a regular part of your operational checklist. Like routine health check-ups, these processes ensure that everything works as it should, free of potential security risks. Investing in these processes is not just a smart business decision but a necessary step in today’s digital age.
—
Discussion on Network Vulnerability Scanning Processes
Network vulnerability scanning processes are not just a technical necessity but an essential business strategy. Given the increasing risks associated with cyber threats, businesses must proactively protect their digital assets. When done correctly, these processes can significantly enhance a company’s security posture, helping to identify and mitigate risks before they result in data breaches or financial losses.
One of the standout features of network vulnerability scanning processes is their ability to provide comprehensive insights into the security status of a network. By uncovering potential weaknesses, these processes allow IT teams to prioritize vulnerabilities based on their severity. It’s like having a detailed roadmap that helps businesses navigate the complex landscape of cybersecurity threats with confidence and precision.
However, it’s important to approach these processes with a critical eye. For the scanning to be effective, it needs to be integrated into a broader cybersecurity strategy. That means using the data gathered from scans to make informed decisions, rather than relying solely on the scans as a silver bullet. It’s there, in the fine print of network vulnerability scanning processes, where businesses will find tremendous value in refining and improving their security practices.
Implementing Effective Strategies
For businesses willing to delve deep, implementing network vulnerability scanning processes is more than a mere checkbox. It’s about integrating security within the company culture. Training employees, continually updating security practices, and investing in the right technologies are essential factors in creating a robust defense against cyber threats.
Addressing Common Misconceptions
There are widespread misconceptions about network vulnerability scanning processes. Some businesses mistakenly believe they are adequately protected once a scan is complete. Others assume such scanning is only for large corporations. But in reality, everyone can benefit from these processes. It’s not just about identifying issues; it’s about creating a proactive environment geared toward total security commitment.
—
Summaries of Network Vulnerability Scanning Processes
—
The Goal of Network Vulnerability Scanning Processes
The primary goal of network vulnerability scanning processes is to identify and remedy security weaknesses before they can be exploited. For businesses of all sizes, the stakes have never been higher. Cyber threats are becoming more sophisticated, leaving organizations at a higher risk of falling victim to attacks. A single breach can compromise critical data, harm reputation, and lead to substantial financial loss. It’s a serious matter, but one that can be navigated effectively with the right tools and strategies.
Achieving a robust security posture requires an ongoing commitment to these processes. Businesses need to view network security as an integral component of their operations, embedding it into their organizational culture. Instead of viewing network vulnerability scanning processes as merely a technical task for IT departments, businesses should involve all departments in understanding its value and role in achieving broader organizational goals. By collectively recognizing the importance and actively engaging in these processes, companies can safeguard their futures in an increasingly uncertain digital world.
Investing in Comprehensive Security
An integral part of network vulnerability scanning processes is investments in comprehensive cybersecurity solutions. Beyond the scanning itself, companies can invest in training, awareness efforts, and innovative security technology to form a multi-layered defense strategy.