- Enhancing Security with Pattern Recognition in Cyber Threats
- The Mechanisms of Pattern Recognition in Cyber Threats
- Implementation Strategies in Cybersecurity Systems
- Effective Steps for Incorporating Pattern Recognition in Cyber Threats
- Bridging the Gap: Discussions on Pattern Recognition in Cyber Threats
- Advanced Insights into Pattern Recognition in Cyber Threats
- Future Trends in Pattern Recognition
- Best Practices for Employing Pattern Recognition in Cybersecurity
- Descriptive Discussion on Pattern Recognition in Cyber Threats
Pattern Recognition in Cyber Threats
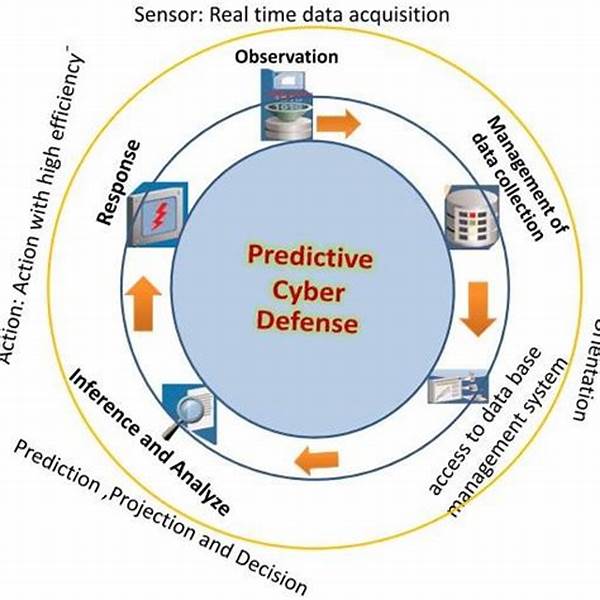
In today’s rapidly evolving digital landscape, cybersecurity threats are more prevalent than ever. Cybercriminals are increasingly sophisticated, making the need for robust defense mechanisms critical for businesses and individuals alike. Enter pattern recognition in cyber threats—a beacon of hope in the war against these digital adversaries. This technique utilizes machine learning and advanced algorithms to identify patterns in malicious activities, aiding in the early detection and mitigation of potential threats. Imagine it as your digital detective, always on high alert, discerning the nuances of cyber threats that traditional systems might overlook.
But why is it a game-changer? Well, pattern recognition not only improves response times but significantly reduces false positives, ensuring cybersecurity professionals can focus on genuine threats rather than sifting through countless alerts. Whether it’s phishing attempts, malware, or ransomware, pattern recognition offers a tailored defense mechanism, giving organizations a competitive edge in cyber defense. With this technology, companies can shift from a reactive to a proactive security posture, preempting attacks before they can cause significant harm.
Enhancing Security with Pattern Recognition in Cyber Threats
Effective pattern recognition in cyber threats requires continuous learning and adaptation. As cyber threats evolve, so too must the algorithms that detect them. Security teams can utilize real-time data feeds to keep their systems updated with the latest threat signatures and patterns. Additionally, by pooling data from various sources, companies can gain a broader understanding of the threat landscape, adapting quickly to new and emerging risks.
Investing in pattern recognition technology is more than just an upgrade; it’s a necessity in today’s digital age. With the cost of data breaches skyrocketing, businesses can no longer afford to stick with outdated security systems. By leveraging pattern recognition tools and techniques, organizations can fortify their defenses, ensuring data integrity and customer trust in an era where cyber threats lurk in every corner of the digital world.
—
The Mechanisms of Pattern Recognition in Cyber Threats
Pattern recognition in cyber threats functions through complex algorithms capable of analyzing vast amounts of data swiftly and accurately. They identify anomalies and predict potential threats based on historical data patterns. Machine learning models can learn from past cyberattacks, recognizing subtle cues that indicate malicious intent. Through iterative learning processes, they become more adept at identifying security breaches before they occur.
Implementation Strategies in Cybersecurity Systems
Implementing pattern recognition requires strategic planning and the right tools. First, assessing the existing security infrastructure is critical. Are your current systems adaptable to new integrations? If not, upgrading is essential. Next, collaborating with cybersecurity experts ensures a seamless transition. Organizations should consider using a hybrid model, combining traditional security practices with pattern recognition techniques, thus maximizing their defense capabilities.
—
Effective Steps for Incorporating Pattern Recognition in Cyber Threats
Bridging the Gap: Discussions on Pattern Recognition in Cyber Threats
Dialogue within the professional community is vital to leveraging pattern recognition effectively. Sharing insights and experiences not only benefits individual organizations but strengthens the collective cybersecurity structure. By discussing successes and failures, professionals can refine their approaches, leading to more efficient and effective strategies.
This collaborative effort extends beyond just the technical aspects; it also involves understanding the human element in cybersecurity. How are people adapting to these technologies? Are they using them as effectively as possible? By examining these questions, organizations can work towards seamless integration of pattern recognition in their broader security frameworks. Together, the cybersecurity community can create a safer digital space by harnessing the power of collective intelligence and cutting-edge technology.
—
Advanced Insights into Pattern Recognition in Cyber Threats
Incorporating pattern recognition into cybersecurity isn’t just about technology—it’s about transforming approaches to digital safety. Companies are reimagining their security protocols, focusing on predictive measures rather than reactionary ones. Statistical analyses reveal that organizations utilizing advanced pattern recognition report a marked reduction in security incidents, further solidifying its role in modern cybersecurity strategies.
Future Trends in Pattern Recognition
Looking to the future, the potential of pattern recognition in cyber threats is immense. With ongoing advancements in AI and machine learning, we anticipate even more precise, efficient systems. These tools will not only predict threats with remarkable accuracy but also adapt to attackers’ evolving strategies, ensuring cybersecurity measures remain a step ahead.
—
Best Practices for Employing Pattern Recognition in Cybersecurity
Descriptive Discussion on Pattern Recognition in Cyber Threats
Businesses across the globe are realizing the power of pattern recognition in cybersecurity. As they integrate these systems into their operations, the payoff has been evident—not only in reduced breaches but also in enhanced workflows and peace of mind. Employees find themselves spending less time grappling with false positives, allowing them to concentrate on genuinely innovative work.
Moreover, pattern recognition transforms the cybersecurity landscape by inviting organizations into a proactive stance. No longer are teams merely responding to breaches; they’re anticipating them, designing systems that can foresee potential weaknesses and bolster them ahead of time. This shift from reactivity to proactivity represents a significant leap in the quality and effectiveness of digital defense strategies. Overall, as organizations embrace these tools, we can expect a safer, more secure digital sphere for everyone involved.
—
By understanding and implementing pattern recognition in cyber threats effectively, organizations not only protect themselves against cybercriminals but also contribute to a safer online environment for everyone. This technology represents a necessary evolution in the digital age—one that is pivotal to securing the future of cyberspace.