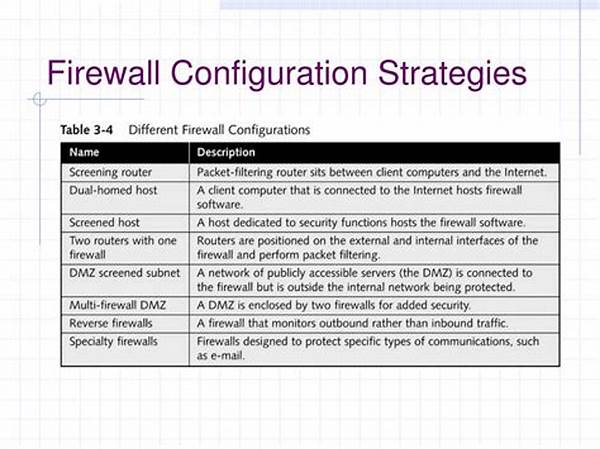
Effective Firewall Configuration Strategies
In today’s fast-paced digital world, safeguarding your data is not a choice but a necessity. Imagine your firewall as the gatekeeper of an ancient kingdom tasked with protecting the treasures within. Your digital assets are those treasures, and effective firewall configuration strategies can be the difference between a security fortress and a vulnerability waiting to be exploited. With cybersecurity threats evolving faster than memes in the digital age, having a robust, well-configured firewall is essential for any organization that values its data.
So, how do you ensure your firewall stands strong against the ever-looming threats? It’s all about employing effective firewall configuration strategies that not only defend but also adapt to newer challenges and threats. By adopting these strategies, you’re not just defending your network but also optimizing it to ensure smooth and efficient operations. It’s akin to having a bodyguard who also happens to provide business consultancy — it’s effective, it’s smart, and it’s a great way to stay ahead.
Strengthening Your Network Fortress
The digital landscape is much like the wild west, where threats lurk in every corner and only the vigilant survive. Effective firewall configuration strategies are your trusted steed and sidearm, ensuring you navigate safely through this volatile environment. Whether it’s setting up strict access controls, monitoring traffic, or simply staying abreast of the latest updates, the components of a robust firewall strategy are varied yet crucial. Moreover, you need something with the robustness of a tank yet the agility of a sports car — tailored exactly to your business needs.
By implementing effective firewall configuration strategies, businesses not only fortify their defenses but also streamline processes, achieving efficiency alongside security. Remember, a well-maintained firewall not only guards against unauthorized access but also maximizes performance. The marriage of utility and security can drive your business to new heights, offering peace of mind and a cutting-edge advantage in a competitive digital landscape.
Understanding the Importance of Configuration
When it comes to cybersecurity, one cannot overlook the importance of configuration. Consider it akin to baking a cake: the ingredients might be there, but without the right measurements and processes, you might end up with a gooey mess instead of a delightful dessert. Effective firewall configuration strategies ensure that your firewall does what it’s supposed to, safeguarding your digital information while allowing legitimate traffic.
Delving Deeper into Firewall Configurations
Firewalls are not just static barriers; they are dynamic, evolving systems that need careful management and adaptation. Discovering the art of balancing security with usability is crucial for every IT manager or business owner. By incorporating effective firewall configuration strategies, we ensure that the right users have access to the right data while keeping malicious actors at bay.
The intricacies of firewall configurations lie in their adaptability — they must evolve with the growing complexity of their threats. As businesses grow and expand their IT systems, they require adaptations and configurations that correspond to their size and function. Hence, the knowledge of configuring firewalls effectively is not just an IT asset but an overall business strategy.
Implementing Advanced Techniques
One of the paramount focuses in today’s digital operations is heightened security protocols through advanced configurations. Effective firewall configuration strategies integrate cutting-edge technology with practical application. By adopting these strategies, organizations can take advantage of features like intrusion prevention systems, user identity filtering, and seamless cloud integration that provide enhanced protection without compromising on speed or user experience.
So, why are effective firewall configuration strategies a game-changer? It’s about aligning your firewall to meet your dynamic business needs, while staying on top of the latest security trends and threats. It’s not just a technical necessity; it’s a competitive edge.
Top 9 Topics Related to Effective Firewall Configuration Strategies
Engaging with Effective Firewall Configuration Strategies
In the digitally driven environment of the 21st century, implementing effective firewall configuration strategies has become more crucial than ever. Organizations are continually striving to stay one step ahead of cybercriminals, who are becoming increasingly sophisticated. The purpose of these strategies is straightforward — to protect sensitive information, maintain the integrity of the data, and ensure a secure communication channel across networks.
Businesses can reap immense benefits by focusing on these best practices. With effective firewall configuration strategies, you are not only protecting your digital assets but also enhancing the overall efficiency of your network operations. Engaging with these methods allows businesses not only to safeguard their current assets but also to build a foundation of security that can adapt to future challenges effortlessly.
Maximizing Firewall Efficiency
Just as a knight wouldn’t head into battle without a full suit of armor, your network should not operate without well-configured firewalls. Effective firewall configuration strategies seek to maximize the efficiency and performance of your digital infrastructure. This involves routine updates, regular monitoring, and a clear understanding of the traffic patterns. With these strategies in place, your firewall becomes not just a barrier but a well-tuned part of a larger security orchestration.
7 Key Points: Effective Firewall Configuration Strategies
The Art of Firewall Strategy
Navigating the world of digital security can often feel akin to steering through a labyrinth. However, with effective firewall configuration strategies at your disposal, you’re equipped with both a map and a compass. Not only do these strategies protect, but they also refine and enhance the operational capabilities of your IT infrastructure.
Adopting the mindset that proactive security is a continuous commitment, organizations can transform their firewalls from mere barriers to dynamic defense mechanisms. By investing in proper configuration, you don’t just prepare for today’s threats — you anticipate tomorrow’s. So, as the digital landscape continues to expand and evolve, your business remains on the cutting edge of security, confidently embracing innovation without sacrificing the safety of its valuable assets.