In the ever-evolving landscape of cybersecurity, understanding and combating advanced persistent threats (APTs) is more crucial than ever. APTs represent a sophisticated form of cyber-attack where an intruder, often backed by well-funded groups or nation-states, gains unauthorized access to a network and remains undetected for an extended period. The primary goal? To extract sensitive information like corporate data, intellectual property, or government secrets. The rise of APTs has necessitated the development of robust analysis techniques to detect and mitigate their impacts efficiently. Enter advanced persistent threat (APT) analysis—a systematic methodology designed to understand the behavior, goals, and techniques of these cyber adversaries.
By employing advanced persistent threat (APT) analysis, organizations can anticipate, recognize, and respond to potential threats. The importance of such analysis cannot be overstated as it equips businesses with the knowledge to shield themselves from financial loss, reputational damage, and even legal challenges. Furthermore, advanced persistent threat (APT) analysis extends beyond mere detection; it includes a strategic component designed to prevent potential infiltration by comprehending and anticipating the intentions and strategies of the adversary.
Advanced persistent threat (APT) analysis isn’t just about technology; it’s about marrying technology with human expertise. Cybersecurity professionals dive deep into vast datasets, sifting through logs and metadata to detect anomalies indicative of threats. These professionals often work in tandem with sophisticated machine learning algorithms that detect patterns that human eyes might miss. This synergy between man and machine represents the cutting edge of cybersecurity defense.
Given the growth of digital transformations across industries, there’s never been a more vital time to incorporate advanced persistent threat (APT) analysis into organizational security frameworks. This detailed scrutiny powers organizations to outsmart adversaries, protect valuable data, and ensure the smooth operation of global infrastructures. Every company, regardless of its size or sector, must consider investing in advanced persistent threat (APT) analysis as part of their broader cybersecurity strategy.
The Importance of Timely APT Detection
The timeliness of APT detection can mean the difference between a thwarted attempt and a catastrophic security breach. Advanced persistent threat (APT) analysis provides organizations with the tools and insights needed to detect threats early. By catching these threats in their infancy, businesses can mitigate significant damage and reduce recovery costs. Prompt detection is not merely reactive; it is proactive and places the organization ahead of the attackers.
—
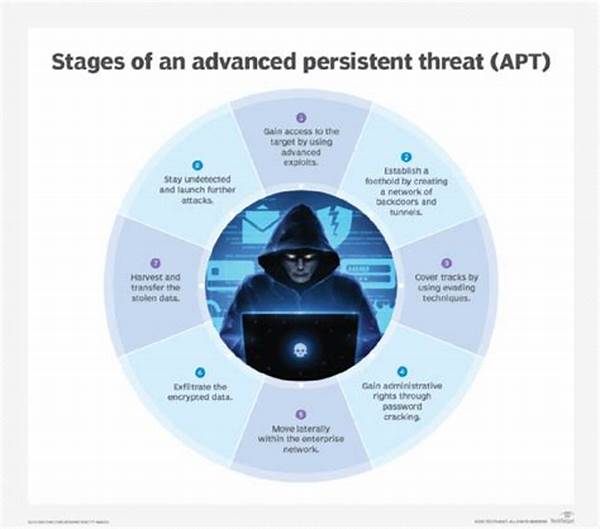
1. Structure of Advanced Persistent Threat (APT) Analysis
Advanced persistent threat (APT) analysis is structured around a series of methodologies that combine technology, intelligence gathering, and human expertise. These methodologies are developed to understand the intricate behavior and goals of APT actors. The primary objective is to analyze these threats to predict their behavior, prepare defenses, and potentially disrupt the attack lifecycle. This approach ultimately helps protect critical assets and confidential data from high-level cyber threats.
Advanced persistent threat (APT) analysis typically begins with identifying and classifying the threat. Cybersecurity professionals use tools to detect anomalies or unusual activities within a network. Once identified, the threat is carefully studied to understand its origin, objective, and scope. This involves tracing the digital footprints of attackers, a challenging but essential process for determining the intent and potential impact of the threat.
Next, advanced persistent threat (APT) analysis requires the integration of threat intelligence. This intelligence comes from a myriad of sources, including industry reports, government warnings, and even dark web reconnaissance. Effective analysis is impossible without up-to-date, accurate intelligence that can inform and enrich the understanding of potential threats.
Following intelligence gathering, cybersecurity teams engage in a detailed review of the technical and behavioral indicators associated with the threat. This detailed analysis provides the context necessary to develop effective countermeasures. Countermeasures can range from enhanced network monitoring, deploying honeypots, to coordinated incident response planning.
Enhancing Cybersecurity with APT Analysis
To add another layer of defense, organizations often incorporate advanced techniques like machine learning into their advanced persistent threat (APT) analysis strategies. These technologies assist in spotting patterns and anomalies that might elude human analysts. By doing so, APT analysis becomes faster, more efficient, and dynamic—adapting quickly to new threats as they emerge.
Understanding the Role of Human Expertise
While technology is a powerful ally, human creativity and analysis remain irreplaceable. Cybersecurity experts offer insights that no algorithm can replicate, making them a crucial part of the advanced persistent threat (APT) analysis process. Their ability to think critically and adapt strategies in real time is essential in this fast-paced digital battlefield.
Key Takeaways on Advanced Persistent Threat (APT) Analysis
In today’s dynamic cyber landscape, the importance of advanced persistent threat (APT) analysis cannot be understated. As organizations strive to maintain security and protect their assets, this form of analysis has become a cornerstone of effective cybersecurity strategy.
Discussion on the Future of APT Analysis
Advanced persistent threat (APT) analysis will continue to evolve as cyber threats become more sophisticated. As organizations globally recognize the significance of cybersecurity, investment in APT analysis technologies and training is expected to rise. Furthermore, the integration of artificial intelligence within this analysis is likely to make threat detection more efficient, reducing the time between threat identification and mitigation.
However, as we look towards the future, challenges remain. The ever-evolving techniques of cyber adversaries mean that APT analysis must also continuously adapt. Cybersecurity professionals will need to stay ahead of the curve, regularly updating their skills and tools to cope with the growing threat. The future of advanced persistent threat (APT) analysis holds both promise and challenges, and it is the responsibility of cybersecurity experts to navigate it strategically.
Incorporating AI in APT Analysis
AI continues to be a game changer in advanced persistent threat (APT) analysis. It assists in parsing through immense datasets to identify patterns and anomalies faster and more accurately than traditional methods. As cybersecurity threats grow in complexity, the role of AI in detection and prevention strategies will become even more critical.
—
10 Key Points of APT Analysis in Cybersecurity
The description of the process of advanced persistent threat (APT) analysis and its integration into cybersecurity strategies is complex, yet it’s transforming the way we approach digital security. This dynamic process involves not just identifying and countering current threats but also predicting and preempting future attacks. Investing in effective advanced persistent threat (APT) analysis can save organizations significant costs and reputational damage associated with breaches. Moreover, the field offers incredible growth opportunities for those interested in making a tangible impact in cybersecurity.
As global connectivity continues to expand, so does the surface area available for potential attacks. Nevertheless, through comprehensive APT analysis, companies can safeguard their assets and uphold trust with their clients and stakeholders. The world of cybersecurity is as thrilling as it is essential, offering a front-seat ticket to an ongoing battle in the digital age. Embracing advanced persistent threat (APT) analysis is not merely a business strategy; it’s a commitment to security in an ever-connected world.