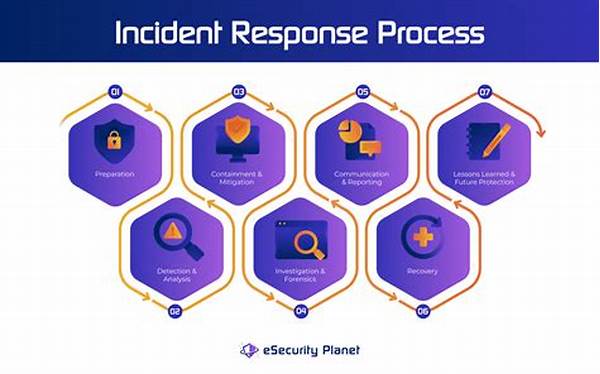
- Incident Response Optimization Techniques
- The Art of Swift Response: A Key In Incident Management
- Improving Incident Response Through Advanced Techniques
- Benefits of Incident Response Optimization Techniques
- Long-Term Goals for Incident Response Optimization Techniques
- Establishing Clear Communication Channels
- Cultivating a Proactive Security Culture
- Leveraging Machine Learning and AI
- Ensuring Compliance with Regulations
- Embedding Continuous Improvement Measures
- Advanced Techniques for Tactical Defence
- Detailed Techniques for Incident Response Optimization
- Objective Analysis of Incident Response Techniques
- Building a Resilient Incident Response Plan
- Five Essential Tips for Effective Incident Response
- Enhancing Your Cyber Strategy with Incident Response
- Quick Guide to Incident Response Optimization Techniques
- Embracing Change: The Key to Cyber Resilience
- The Human Element
Incident Response Optimization Techniques
In the fast-paced digital world, where every click and tap can lead to a cascade of data, the importance of having robust incident response strategies cannot be overstated. Remember the days when simply having an antivirus software was considered tech-savvy? Those days are long gone. Cyber threats are getting smarter, and so should your response to them. Enter the era of incident response optimization techniques—your knight in shining armor.
Imagine this: It’s a busy Monday morning. You’ve just settled into your chair with a fresh cup of coffee when you notice something peculiar on your screen. Notifications are pinging crazily; your email inbox is a deluge of unexpected alerts. Panic? Not you. Armed with incident response optimization techniques, you’re as calm as a duck on a pond (even if your feet are paddling madly underwater). You know you’re just seconds away from saving the day with your well-prepared action plan.
These optimization techniques are not just about averting disasters; they’re about transforming potential threats into opportunities for growth. By fortifying your defenses, you’re not only shielding your business but also reassuring your customers that you’re the steadfast guardian of their data. It’s almost like wearing a virtual superhero cape while sipping your now-cold coffee!
Want to learn the secrets of these techniques? Buckle up, because we’re about to take you on a humorous, engaging, and insightful tour into the world of incident response optimization techniques—where every bit counts and every second saves the day.
The Art of Swift Response: A Key In Incident Management
Incident response optimization techniques are all about speed and precision. The faster you can detect and respond to an incident, the less damage it can cause. Remember those old Westerns where the hero draws his gun at lightning speed? That’s you, with your incident response plan. Swift response is the heart and soul of these techniques, ensuring that you can extinguish threats before they spiral out of control.
Your incident response strategy should be like a well-choreographed dance. Every team member knows their role; every step is precise and deliberate. Coordination is key. So, during that Monday morning kerfuffle, not only do you act fast, but your team moves like a symphony, each note ringing perfectly in tune with the others.
But what happens when the unexpected occurs? Even the most detailed plans can fall prey to the unknown. This is where adaptability enters the scene. Incident response optimization techniques equip you with the flexibility to pivot swiftly, adapting to new challenges even as they emerge.
Never underestimate the power of practice, too. Like a seasoned athlete, constant drills ensure your incident response team can leap into action with confidence. Regular training sessions transform into your digital gym, keeping your skills honed and ready for any cyber battle that lurks.
Improving Incident Response Through Advanced Techniques
The tales of cybersecurity are endless. For every new threat, there’s a more ingenious solution. So how do you keep your strategies sharp? By diving into advanced incident response optimization techniques, you can turn the tides in your favor effortlessly.
Automation is a buzzword you can’t ignore. Picture it as your cyber-sidekick: tirelessly pulling logs, sending alerts, and even initiating the first steps of your incident response plan faster than you can say “cybersecurity.” Partnering with machine learning technologies, these tools can predict potential threats with almost uncanny accuracy—before they even happen.
And then there’s the power of big data. Imagine having a crystal ball that grants you insights into threat patterns. Well, it’s not exactly magic, but data analytics come remarkably close. By analyzing past incidents, spotting patterns, and predicting future risks, you’re not reacting but proacting—in essence, staying one step ahead of those pesky villains.
Communicate, and often. During an incident, keeping everyone informed can be the difference between chaos and control. Whether it’s through a group chat, a designated emergency line, or smoke signals (just kidding!), fostering clear communication is indispensable.
Benefits of Incident Response Optimization Techniques
Ultimately, what good are all these plans and practices if you don’t see tangible benefits? Fortunately, incident response optimization techniques provide a slew of them. From a business standpoint, minimizing downtime is crucial. Imagine how much productivity could plummet when systems go down. Optimized response times ensure you’re back online before employees even finish their muted and painfully awkward Zoom video call.
And then there’s customer trust. Maintaining a robust incident response not only saves you from catastrophic data breaches but also builds your reputation as reliable and secure—a paragon of the digital realm. And in today’s market, trust is as valuable as gold.
Working on an optimized plan also makes financial sense. While investing in these techniques seems a sizable commitment upfront, the potential savings during an incident response are monumental—funds not spent recovering from an attack count as a direct benefit to your bottom line.
Let’s face it, in the chaotic realm of cyberspace, there’s nothing more comforting than being confident that your defenses are ironclad. Having robust incident response optimization techniques is your beacon of hope—a fortress against the impending digital storm.
—
Long-Term Goals for Incident Response Optimization Techniques
In the ever-evolving digital landscape, defining clear goals when implementing incident response optimization techniques is pivotal. With cyber threats looming larger than ever, positioning your organization as a leader in proactive response can be a game-changer. By developing a well-structured roadmap, you ensure you’re not merely reacting to incidents but strategically managing them.
Establishing Clear Communication Channels
One core objective is the establishment of robust communication channels. In crisis situations, information must flow seamlessly. Imagine trying to pass a message during a game of broken telephone, only it’s your business at stake. Effective incident response optimization techniques ensure that everyone, from IT to PR teams, knows exactly what to do when chaos ensues.
Exploring technologies like instant messaging, incident management platforms, or even AI chatbots can facilitate real-time communication. By integrating these tools, the noise of confusion fades, leaving room only for clarity and swift action.
Cultivating a Proactive Security Culture
Another crucial aim is cultivating a culture of vigilance. Your team is your first line of defense and inculcating a proactive security mindset can exponentially amplify the effectiveness of incident response optimization techniques. Encouraging routine exercises, knowledge-sharing sessions, and continuous learning fosters an environment where preparedness is second nature.
Picture this: your office is a beehive of activity, with each member diligently protecting their digital honey. An engaged workforce becomes your human firewall, adeptly managing threats with tact and precision.
Regular audits, penetration testing, and up-to-date training are meticulous methods to galvanize this culture. The goal is transformation—an evolution from passive employees to proactive guardians of digital sanctuaries.
Leveraging Machine Learning and AI
As technology progresses, so should your techniques. Another long-term goal is leveraging machine learning and AI to optimize these responses. A smart system that predicts and learns from past behavior dramatically shifts fates from reactive to predictive.
The beauty of AI lies in its unerring ability to analyze vast amounts of data swiftly. Through incident response optimization techniques designed around AI frameworks, systems can deploy patches, isolate threats, and execute defenses with machine precision.
Ensuring Compliance with Regulations
In the realm of regulatory landscapes, ensuring compliance becomes another pivotal aim. With data protection laws tightening globally, aligning your response techniques with industry regulations shields you from heavy penalties and reputational damage.
Think of regulations as the guardrails on your incident response highway; they ensure you’re not veering off into perilous terrains. Following global standards not only boosts your credibility but keeps you firmly within the boundaries of legal safety.
Embedding Continuous Improvement Measures
Lastly, embedding a philosophy of continuous improvement defines the avant-garde in incident response optimization techniques. A static defense strategy is a vulnerable one; evolving threats demand evolving responses.
Post-incident reviews, feedback loops, and metric-driven assessments allow for continuous refinement. These evaluations are the whetstone, constantly sharpening your incident response sword—a sword capable of cutting through any cyber entanglement.
Advanced Techniques for Tactical Defence
To encapsulate, defining long-term goals around incident response optimization techniques we risk-proof the future and simulate resilience. By strategically embedding these efforts, organizations not only surge ahead of possible catastrophes but seamlessly embed strategies and systems that transform risks into opportunities, and threats into reassuring challenges.
Building such a robust, adaptable, and forward-thinking incident response framework isn’t just smart—it’s crucial. Because in the swirling vortex of ones and zeroes, staying prepared is not just an option—it’s survival.
—
Detailed Techniques for Incident Response Optimization
Objective Analysis of Incident Response Techniques
In today’s digital age, the race to keep up with emerging cyber threats is relentless. Organizations can no longer afford to react; they need a proactive stance facilitated by incident response optimization techniques. The overarching goal? Seamless integration of these techniques into the everyday operations—a move that ensures safety, efficiency, and financial prudence.
Central to this is automation. By automating response procedures, businesses mitigate risk exposure even before human intervention. Think of it as having a dedicated sentinel that never sleeps, constantly on the lookout for potential breaches and neutralizing them without a hint of delay.
Team training is another pillar of strength. Routine drills mimic real-life scenarios, preparing your team for the unpredictable nature of attacks. It’s like fire drills; only in this case, the fire is a barrage of zeros and ones. This readiness transforms mere reaction into confident, efficient action.
In essence, the goal is clear: embed a culture of security in every fiber of the company. With incident response optimization techniques leading the charge, you’re not just preventing data breaches; you’re building a fortress in the digital space, one that grows stronger with every challenge faced.
—
Building a Resilient Incident Response Plan
Incorporating effective incident response optimization techniques can make the difference between surviving a cyber threat and succumbing to it. But how can a company bolster its defenses? Here are some expert tips:
Five Essential Tips for Effective Incident Response
Enhancing Your Cyber Strategy with Incident Response
Imagine the chaos of a cyber breach without incident response optimization techniques in place—like knights without armor on a battlefield. A sound incident response plan is foundational, and these tips are your blueprint for creating one that acts not just as a reactionary measure but as a proactive shield.
A detailed plan ensures every team member knows their role and the steps necessary to mitigate damage. Your devoted response team acts like the elite squad in espionage movies, ready to tackle incidents at a moment’s notice. Meanwhile, investing in cutting-edge technologies equips them with tools that amplify their abilities—a digital Excalibur of sorts.
Regular drills transform your team from mere spectators into elite players in the digital arena, prepared to face threats with agility and precision. And when you enrich this framework with external intelligence, your defense becomes a well-rounded force ready to take on the ever-changing landscape of cyberspace.
In short, incident response optimization techniques aren’t just about surviving the storm; they’re about weathering it with grace and emerging stronger on the other side.
—
Quick Guide to Incident Response Optimization Techniques
In the wild west of cyber warfare, incident response optimization techniques are your trusty sidekick, your beacon and compass all rolled into one. Juggling between planning and execution may feel like walking a tightrope—without them, you’d likely tumble into chaos. But mastering their art doesn’t require wizardry. Here’s a quick guide to understanding and applying these remarkable techniques effectively.
Embracing Change: The Key to Cyber Resilience
Understanding the need for continual learning is paramount. Just as hackers evolve, so must your strategies. The digital landscape is dynamic, and remaining static is not an option. By implementing incident response optimization techniques, businesses can pivot, adapt, and ultimately persevere amidst uncertainty.
This remarkable thing about these techniques is that they offer you a kind of immunity—a shield against the terrors lurking in the cyber shadows. By embracing tools like machine learning, you empower your teams to diagnose, detect, and even anticipate trouble before it unfolds.
The Human Element
It turns out that the human element remains irreplaceable. Machines may process data at lightning speed, but it’s your skilled professionals who infuse creativity, critical thinking, and emotional intelligence into the mix—skills no CPU can replicate. Cultivating a thriving security culture in your organization, therefore, becomes a potent pillar for success.
In reality, the real magic happens when your team aligns, communicating effortlessly, prepared to act as one in times of need. Think of incident response optimization techniques as the orchestra, and your cyber warriors as the musicians—together they can create a symphony of security.
In conclusion, embracing incident response optimization techniques isn’t a minimally mandatory task—it’s a compelling necessity. When integrated with passion and precision, these strategies are not merely functional; they amplify your organization’s resilience, allowing you to face the future with fortified confidence.