Certainly! Let’s begin by crafting an engaging piece about “network perimeter security controls.”
—
In an ever-evolving digital landscape, safeguarding sensitive data is the linchpin to sustaining business operations and achieving consumer trust. Network perimeter security controls stand at the forefront of this effort, acting as the digital fortress that shields your internal networks from external threats. Imagine your network as a medieval castle, complete with walls and drawbridges—now visualize perimeter security controls as the vigilant guards ensuring only trusted visitors pass through the gates. With cyber threats continually looming and attackers growing increasingly sophisticated, businesses can no longer rely on basic defenses. Enter the robust, dynamic, and undeniably critical world of network perimeter security controls.
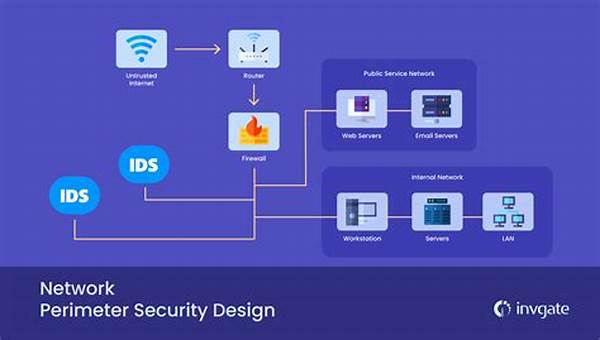
At its core, network perimeter security involves a series of defined security measures that encompass firewalls, intrusion detection systems, and virtual private networks (VPNs). The concept is simple yet profound: prevent unauthorized access while allowing legitimate traffic to flow seamlessly. However, making the right choice of these controls can significantly bolster your defense strategy, ensuring data integrity and privacy without stifling operational efficiency. For organizations wondering how to gracefully manage this balance, investing in comprehensive network perimeter security controls is the answer.
Adding to the allure of these controls is their adaptability and customizability. Businesses from the mom-and-pop store on Main Street to the sprawling conglomerate can tailor their perimeter security to fit precise needs and budgets. Picture the peace of mind knowing your sensitive data, customer information, and proprietary secrets are locked behind an impenetrable digital barricade. Choosing the right security controls is not just a tech-savvy move; it’s a proactive strategy for sustaining brand reputation and customer loyalty in today’s data-driven marketplace.
The Essentials of Network Perimeter Security Controls
Network perimeter security is layered with technologies designed to create barriers against unauthorized access. From state-of-the-art firewalls to sophisticated intrusion detection systems, each piece plays a critical role in the holistic protection framework.
—
Strategic Importance of Network Perimeter Security Controls
In the bustling marketplace of cyber solutions, network perimeter security controls ascend as not only a necessity but a defining component of any robust cybersecurity strategy. Imagine a bustling small business that suddenly faces a cyber-attack—financial data exposed, customer trust eroded, and recovery costs through the roof. That’s when network perimeter security goes from “nice-to-have” to “essential.”
For instance, a recent study highlights how businesses implementing comprehensive perimeter controls experienced a 40% decrease in successful cyber-attacks. Why? Because they were equipped with firewalls that monitor and control incoming and outgoing network traffic based on predetermined security rules. Such statistics aren’t just numbers; they translate into real-world impact—safer transactions, satisfied customers, and a resilient reputation.
Beyond the numbers, however, lies the narrative of adaptation and foresight. In today’s corporate environment, where every digital loophole can become a massive vulnerability, integrating network perimeter security controls isn’t just about protection. It’s about preparing an establishment to thrive in the intricacies of the digital age. This foresight breeds confidence and a proactive approach towards change, addressing not just today’s, but tomorrow’s cyber challenges.
Network Perimeter Security: A Multi-Layered Approach
Perimeter security is far from a single-layered battle shield. In truth, it’s a myriad of sophisticated solutions combining to provide seamless protection. Firewalls are often your first line of defense, filtering incoming and outgoing internet data to deter threats. Next, intrusion detection systems act like your very own cyber detectives, identifying suspicious actions that could precede an attack. And VPNs? Think of them as secure communication highways—encrypting data to keep it away from prying eyes.
Common Features of Network Perimeter Security Controls
Evaluating network perimeter security controls doesn’t stop at choosing the component—it involves scrutinizing the features they offer. Is the firewall capable of deep packet inspection? How adaptable is the intrusion detection system to new threat signatures? Answering these questions helps tailor the security measures to suit the precise needs of the organization.
Unraveling the Mechanisms
To truly appreciate these features, one must delve into their mechanisms. Take a firewall, for example. Within its virtual boundaries, it monitors data packets traveling across a network, allowing those it deems safe while blocking any deemed harmful. Fascinating, right?
This mechanism enhances security by establishing trust boundaries and implementing rule-based filtering to prevent unauthorized access. Meanwhile, intrusion detection systems work behind the scenes to add additional layers of scrutiny.
Balancing Security Controls and Accessibility
The crux of network perimeter security controls lies in their ability to balance security and accessibility. Striking this balance ensures that while threats are effectively neutralized, legitimate traffic and operations remain uninterrupted. This equilibrium guarantees businesses can persevere without compromising user experience or efficiency.
With each passing day, investing in refined network perimeter security controls positions organizations not just to withstand inevitable cyber challenges, but to also innovate and excel. It’s a commitment to progress and protection, a pledge to uphold trust and reliability in an interconnected world.
—
Discussion Topics on Network Perimeter Security Controls
Understanding how multi-layered security frameworks, combining various controls, strengthen defense mechanisms.
Discuss the evolving nature of cyber threats and how security controls need to adapt to these changes.
Weighing the financial investment in security controls against potential savings from avoided breaches.
Exploring new technologies such as AI and machine learning and their application in enhancing perimeter security.
A look at how small businesses benefit from well-integrated perimeter security controls.
By constantly evolving alongside technology and threats, network perimeter security controls have become pivotal aspects of a company’s cybersecurity arsenal. Not only are these controls about fortifying network defenses; they are the bridge between maintaining everyday business operations and optimizing innovation securely. As technology continues to forge forward, so too must our commitment to safeguarding what makes a business tick—reliable, uninterrupted connectivity, and trust.